
FORENSE DIGITAL (DIGITAL FORENSICS)
COMPUTER, CLOUD, MOBILE, MEMORY, OS, SOFTWARE AND NETWORK FORENSICS
COMPUTER, CLOUD, MOBILE, MEMORY, OS, SOFTWARE AND NETWORK FORENSICS
 LIVROS E PUBLICAÇÕES
LIVROS E PUBLICAÇÕES
 EVENTOS
EVENTOS
 ARTIGOS
ARTIGOS
 VÍDEOS
VÍDEOS
 INFOGRÁFICOS
INFOGRÁFICOS
 ORGANIZAÇÕES
ORGANIZAÇÕES
 FERRAMENTAS (TOOLS)
FERRAMENTAS (TOOLS)
 WEBINÁRIOS
WEBINÁRIOS
 PODCASTS
PODCASTS
 BLOGS
BLOGS
PUBLICAÇÕES (LIVROS, E-BOOKS, RELATÓRIOS e PERIÓDICOS)


e-book - Let's learn tcpdump!
By Julia Evans| Wizard Zines |
Ever wanted to know how to use tcpdump, but were intimidated by all the command line options? I was too! But then I learned it, and it wasn’t as bad as I thought. In this zine we’ll explain: what kinds of questions you can answer with tcpdump; how to interpret tcpdump output; which command line arguments are the really important ones and how to write a BPF filter to filter tcpdump output


REPORTS - INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA)
Strategic, policy and tactical updates on the fight against cybercrime.
The IOCTA reports are Europol’s flagship strategic products highlighting the dynamic and evolving threats from cybercrime. It provides a unique law enforcement focused assessment of emerging challenges and key developments in the area of cybercrime.


GUIDE - FRAMEWORK FOR RESPONDING TO A DRONE INCIDENT, Second Edition - January, 2020
For First Responders and Digital Forensics Practitioners
This INTERPOL Framework for Responding to a Drone Incident provides guidelines for First Responders and Digital Forensics Practitioners on how to respond to a drone incident. The framework is intended to provide technical guidance in managing and processing an incident.


GUIDE - Electronic Crime Scene Investigation: A Guide for First Responders, Second Edition - April, 2008
This guide is intended to assist State and local law enforcement and other first responders who may be responsible for preserving an electronic crime scene and for recognizing, collecting, and safeguarding digital evidence.

GUIDE - GUIDELINES FOR DIGITAL FORENSICS FIRST RESPONDERS, Second Edition - April, 2008
Best practices for search and seizure of electronic and digital evidence
These Guidelines aim to establish best practices for handling and using digital evidence during search and seizure preparatory and execution stages. Key technical considerations are also identified on the effective preservation of data to ensure that it can support law enforcement in criminal investigations, and it can be admissible in court.


GUIDE - IoT Investigação Forense Digital: Fundamentos e Guia de Referências
Por João Roberto Peres e Cristina Moraes Sleiman | Komp | - 1a Edição, Novembro 2017
Este documento foi concebido como contribuição aos interessados nos temas relacionados a “Procedimentos de Investigação Forense Computacional em crimes cibernéticos associados à Internet das Coisas IoT ”bem como em assuntos correlatos a IoT/IoE,entre outros.


GUIDE - Memory Forensics: Framework & Workbench
Memory Forensics is a budding field in Digital Forensics Investigation which involves recovering, extracting and analysing evidence such as images, documents, or chat histories etc from the structured volatile memory into non-volatile devices like Hard-drives or USB drives.

EVENTOS


CONFERENCE 22 to 26 Nov 2021 - Forensic Experts Forum 2021 CONFERENCE
The Forensic Experts Forum brings together all relevant players within law enforcement, private industry and academia to exchange knowledge, expertise and experience, but also to identify new trends, developments and best practices in digital forensics. FEF 2021 will be a week-long conference with 3 hours sessions per day.


PALESTRAS 1999-2021 - Palestras Proferidas pelo CERT.br
Página onde estão disponíveis os materiais das palestras proferidas pelo Centro de Estudos, Resposta e Tratamento de Incidentes de Segurança no Brasil (CERT.br) entre 1999 e 2021 sobre práticas de seguranca, resposta a incidentes e atuação de grupos de resposta a incidentes de segurança. Contém documentos estão em formato PDF e links para vídeos das apresentações.




VÍDEOS


Vídeo - Titanium Project: Seven Steps to Combat Cybercrime)
Latest video of the Titanium Project (closed on 2020-04-30).



Vídeo - Canal no Youtube do Prof.Marcos Monteiro
Especializado em Computação Forense


Latest video of the Titanium Project (closed on 2020-04-30).



Especializado em Computação Forense



ARTIGOS CIENTÍFICOS (Papers)


Paper - D4I - Digital forensics framework for reviewing and investigating cyber attacks - by Athanasios Dimitriadis, Nenad Ivezic, Boonserm Kulvatunyou and Ioannis Mavridis at Array Volume 5, March 2020


Paper - Digital Forensic Investigation of Social Media, Acquisition and Analysis of Digital Evidence - by Reza Montasari, Richard Hill, Victoria Carpenter, Farshad Montaseri (University of Huddersfield, UK) at International Journal of Strategic Engineering (IJoSE), 2019


TEXTOS BÁSICOS E LEITURAS COMPLEMENTARES (Basic Readings)


Reading - What is digital forensics? - by NIST Forensic Science at nist.gov

Reading - What is digital forensics? - by EC Council


ARTIGOS


Artigo - Cadeia de custódia de computação forense no Azure
Por Staff | Microsoft | Acesso em 2022
A análise forense digital é uma ciência que aborda a recuperação e a investigação de dados digitais para dar suporte a investigações criminais ou processos civis. A computação forense é uma ramificação da análise forense digital que captura e analisa dados de computadores, VMs (máquinas virtuais) e mídia de armazenamento digital.
As empresas precisam garantir que as evidências digitais fornecidas por elas em resposta a solicitações legais demonstrem uma CoC cadeia de custódia válida em todo o processo de aquisição, preservação e acesso de evidências. Para garantir uma CoC válida, o armazenamento de evidências digitais precisa demonstrar controle de acesso, proteção e integridade de dados, monitoramento e alertas adequados, bem como log e auditoria.
Article - USB Forensics – Reconstruction of Digital Evidence from USB Drive
By BALA GANESH | GBHackers on Security | June 19, 2022
Digitial Forensics analysis of USB forensics include preservation, collection, Validation, Identification, Analysis, Interpretation, Documentation, and Presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal.

Article - Most Important Computer Forensics Tools for Hackers and Security Professionals
By BALAJI N | GBHackers on Security | August 21, 2022
Computer Forensics tools are more often used by security industries to test the vulnerabilities in network and applications by collecting the evidence to find an indicator of compromise and take appropriate mitigation Steps. In this article you can find the Comprehensive Computer Forensics tools list that covers Performing Forensics analysis and responding to the incidents in all the Environments

As empresas precisam garantir que as evidências digitais fornecidas por elas em resposta a solicitações legais demonstrem uma CoC cadeia de custódia válida em todo o processo de aquisição, preservação e acesso de evidências. Para garantir uma CoC válida, o armazenamento de evidências digitais precisa demonstrar controle de acesso, proteção e integridade de dados, monitoramento e alertas adequados, bem como log e auditoria.



BLOGS E FÓRUNS DE DISCUSSÃO


Blog - Perícia forense computacional
Por João Eriberto Mota Filho |
Blog - CyberCrime & Doing Time
A Blog about Cyber Crime and related Justice issues (by Gary Warner - Director of Research in Computer Forensics)

Blog - ZENA FORENSICS
something about digital forensics and something not
By Mattia Epifani | digital-forensics.it | Last access Jan, 2024

INFOGRÁFICOS


Infographic - What is Digital Forensics?
By Staff | Lawrence Ryan Investigations | Last Acess 2023
Digital forensics is a branch of forensic science that focuses on identifying, preserving, recovering, analyzing, and presenting facts found on digital devices, like: computers, memory cards, external hard drives, smartphones and servers. In other words, any device that stores data can be subject to digital forensic investigations.

Infographic - Top Digital Forensics Tools
By G. M. Faruk Ahmed | Linkedin Post | Nov, 2023

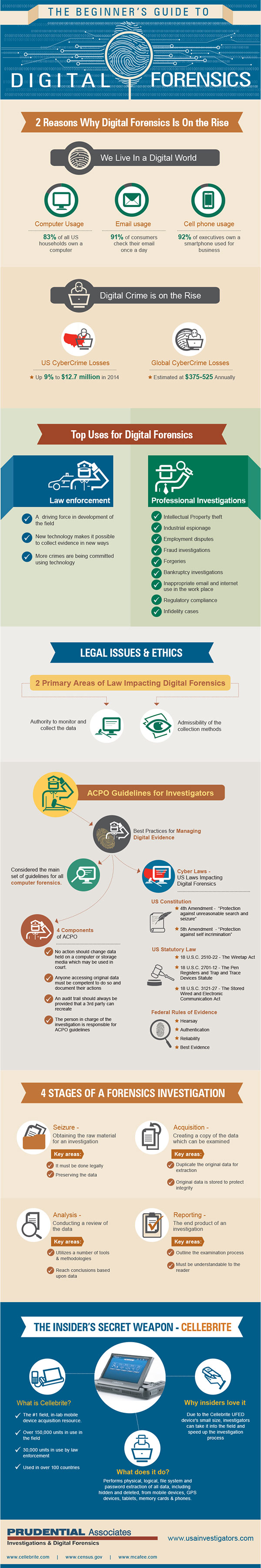
Infographic - A Beginner’s Guide to Digital Forensics – Infographic
By Staff | Prudential Associates | Nov, 2023
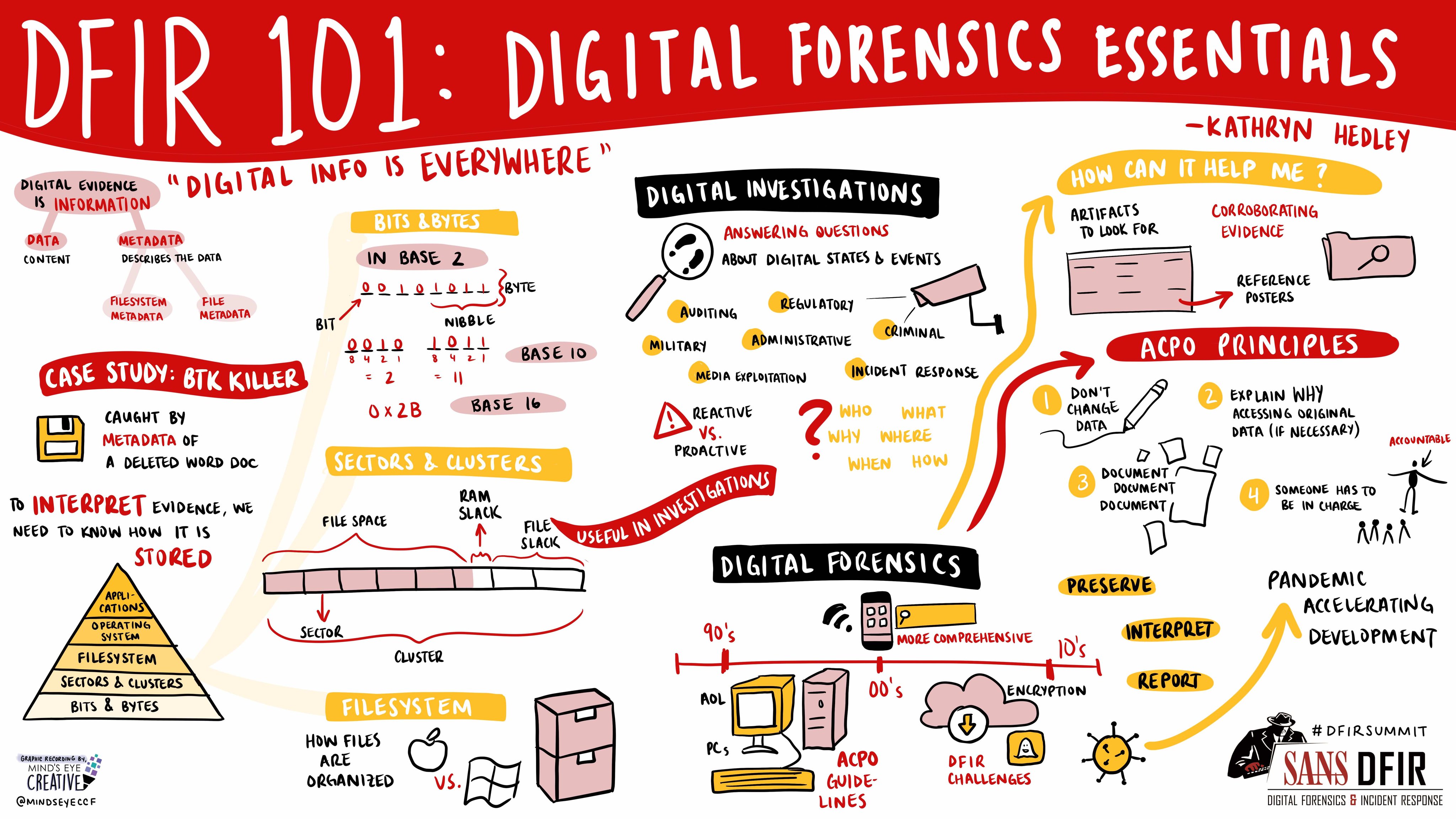
Infographic - DFIR 101: Digital Forensics Essentials
By Kathryn Hedley, Associate Instructor | SANS Institute | 2021
Infographic - OpenSCAP Tools
By OpenSCAP | OpenSCAP.org | Last Acess 2024


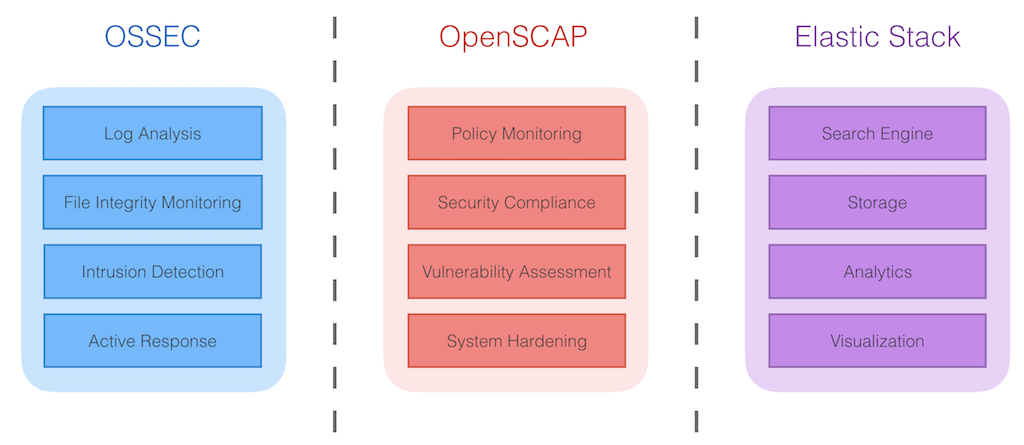
Infographic - OSSEC, OpenSCAP and Elastic Stack
By Staff | Guia do TI | Last Acess 2024





ÓRGÃOS, AGÊNCIAS, ASSOCIAÇÕES, CONSÓRCIOS, PARCERIAS, ALIANÇAS E COMUNIDADES


ONVIF - ONVIF is an open industry forum that provides and promotes standardized interfaces for effective interoperability of IP-based physical security products.

CSOFS - The Chartered Society of Forensic Sciences is an internationally recognised professional body with members in over 60 countries. The Society will ensure that it: (1) promotes & develops regulation in forensic science & practice; (2) provides opportunities for education, training & development for forensic practitioners; (3) supports and encourages research & development in the forensic sciences; and (4) strives to continuously improve its internal structure & finances.

Digital Forensics Skills
In assessing the skills appropriate for the digital forensic practitioner there are two key types of core skills important in providing reassurance to employers: general transferable skills and key practical skills.

Digital Forensics v2021-1
The purpose of Digital Forensics v2021-1 is to equip students with an understanding of the theory and application of analytical methods commonly used in digital evidence examination, recovery & preservation. In addition to equip them to provide justified evaluation and interpretation of the results of analysis for the purposes of intelligence, investigation including those reaching the justice system.

ANPD - Criada em 2018 , a Autoridade Nacional de Proteção de Dados (ANPD) tem como missão institucional assegurar a mais ampla e correta observância da Lei Geral de Proteção de Dados Pessoais – LGPD (Lei n. 13.709, de 2018) no Brasil e, nessa medida, garantir a devida proteção aos direitos fundamentais de liberdade, privacidade e livre desenvolvimento da personalidade dos indivíduos. O art. 55-J da LGPD estabelece as principais competências da ANPD. A sua estrutura regimental foi aprovada em 2020 (Decreto N° 10.474, de 26 de agosto de 2020)

CERT.BR - O Centro de Estudos, Resposta e Tratamento de Incidentes de Segurança no Brasil é mantido pelo Núcleo de Informação e Coordenação do Ponto BR (NIC.br), do Comitê Gestor da Internet no Brasil, e atende a qualquer rede brasileira conectada à Internet. O NIC.br é uma organização privada sem fins lucrativos criada para implementar as decisões e os projetos do CGI.br, que é o responsável por coordenar e integrar as iniciativas e serviços da Internet no país. Sua missão é aumentar os níveis de segurança e de capacidade de tratamento de incidentes das redes conectadas à Internet no Brasil. Como Grupo de Resposta a Incidentes de Segurança (CSIRT) de Responsabilidade Nacional, opera em conformidade com a RFC2350
(https://datatracker.ietf.org/doc/html/rfc2350)

ENISA - Fundada em 2004, a Agência Europeia para a Segurança das Redes e da Informação (European Union Agency for Cybersecurity - ENISA) é um organismo da União Europeia que visa ajudar a garantir um elevado nível de segurança nas redes de informação e nos respectivos dados, através da recolha de informação, da análise de riscos e de acções de sensabilização e promoção das melhores práticas.

NCSC - The National Cyber Security Centre
Launched in October 2016, the NCSC has headquarters in London and brought together expertise from CESG (the information assurance arm of GCHQ), the Centre for Cyber Assessment, CERT-UK, and the Centre for Protection of National Infrastructure.

EUROPOL - European Union’s law enforcement agency.
Europol main goal is to achieve a safer Europe for the benefit of all the EU citizens.
Cybercrime is a growing problem for countries, such as EU Member States, in most of which internet infrastructure is well developed and payment systems are online. The response of Europol and its partners must itself be comprehensive, dynamic and relentlessly innovative. And it is, pursuing cybercriminals on all fronts.

In assessing the skills appropriate for the digital forensic practitioner there are two key types of core skills important in providing reassurance to employers: general transferable skills and key practical skills.
The purpose of Digital Forensics v2021-1 is to equip students with an understanding of the theory and application of analytical methods commonly used in digital evidence examination, recovery & preservation. In addition to equip them to provide justified evaluation and interpretation of the results of analysis for the purposes of intelligence, investigation including those reaching the justice system.
FERRAMENTAS (TOOLS), SOFTWARES E APLICAÇÕES


TOOLS - 10 Best Free Forensic Investigation Tools – 2022
By Guru| Cybersecurity News | June 25, 2021
Forensics’s history is evolved over the decades in different branches of forensic science. It has become a very crucial part of enforcement activities throughout the globe. here we have listed some of the most important 10 Free Forensic Investigation Tools that help to fight against cybercrime and protect digital assets.
➼ Sleuth Kit (+Autopsy)
➼ Forensic Investigator
➼ Autopsy
➼ Dumpzilla
➼ Browser History
➼ FTK Imager<
➼ X-Ways Forensics
➼ CAINE
➼ Toolsley
➼ ExifTool

NIST - NSRL
The NSRL is The National Software Reference Library, based out of the National Institute of Standards and Technology, an agency of the U.S. Department of Commerce. The NSRL project is supported by the U.S. Department of Homeland Security, federal, state, and local law enforcement, and the National Institute of Standards and Technology (NIST) to promote efficient and effective use of computer technology in the investigation of crimes involving computers. It has three components: (1) a large collection of software packages; (2) a database containing detailed information, or metadata, about the files that make up those software packages; and (3) a public dataset, the NSRL Reference Data Set (RDS) which contains a subset of the metadata held in the database for each file in the collection. The RDS is published and updated every three months.
CLOUD - Top 11 Open Source Cloud Security Tools to Protect Data from Hackers
These Cloud Security Tools are useful for any public and private models like SaaS, PaaS, laaS, etc. This is completely built and operates through open-source technologies.
➼ GoAudit
➼ Grapl
➼ Kali Linux
➼ KeePass
➼ Metasploit Framework
➼ Osquery
➼ OSSEC
➼ Panther
➼ Suricata
➼ Wazuh Cloud
➼ Zeek/Bro


AUDITING TOOLS - Handy Tips: Top Cybersecurity auditing tools in 2021
By Disha Sinha October | analyticsinsight.net/ | 14, 2021
Network security auditing tools
Audit tools are essential to protect business from malicious actions. The article explores some of the useful cybersecurity auditing tools (network security auditing tools) for identifying potential security risks and fix those efficiently and effectively.
➼ Intruder
➼ OpenVAS
➼ SolarWinds Network Configuration Manager
➼ Nessus
➼ Syxsense Manage

TOOLS - https://en.wikipedia.org/wiki/List_of_digital_forensics_tools
From Wikipedia, the free encyclopedia | Wikipedia/ |
During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. This first set of tools mainly focused on computer forensics, although in recent years similar tools have evolved for the field of mobile device forensics.[1] This list includes notable examples of digital forensic tools.

TOOLS - Conheça 5 distros Linux para Pentest
By Staff | hackersec.com | September, 2021
5 distros usadas por hackers e profissionais de cibersegurança para pentest, engenharia reversa, forense, análise de malware, web hacking e entre outros.

TOOLS - Indexador e Processador de Evidências Digitais (IPED) / IPED Digital Forensic Tool
Por Coordenação Geral de Tecnologia da Informação (CGTI)/Serviço de Perícias em Informática (SEPINF) | DPF | 2022
Programa linha de comando em java originalmente desenvolvido pela para indexar relatórios do FTK 1.8 (convertidos pelo AsAP3) e relatórios do FTK 3+. Atualmente apresenta diversas funcionalidades presentes em softwares forenses comerciais, servindo como alternativa eficiente e de código aberto na maioria dos casos. Tem como objetivos: (1) facilitar a visualização de Laudos de extração de dados por parte da equipe de investigação e melhorar a qualidade de Laudos contendo resultados de pesquisas por palavraschave; e (2) facilitar a análise dos dados em soluções de SARD, como a descrita em Triagem de Mídias SETEC/DF. Foi desenvolvido pela Coordenação Geral de Tecnologia da Informação (CGTI) do Departamento de polícia Federal (DPF) do Brasil
IPED is an open source software that can be used to process and analyze digital evidence, often seized at crime scenes by law enforcement or in a corporate investigation by private examiners.
MANUAL

Repositório no github

TOOLS - OSINT-FORENSICS-MOBILE
From CScorza | Github |
During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. This first set of tools mainly focused on computer forensics, although in recent years similar tools have evolved for the field of mobile device forensics.[1] This list includes notable examples of digital forensic tools.


AccessData FTK Imager: https://www.exterro.com/ftk-imager
AccessData Forensic Toolkit (FTK): https://www.exterro.com/ftk-digital-forensics
Autopsy: https://www.sleuthkit.org/autopsy/
Autopsy® is an easy to use, GUI-based program that allows you to efficiently analyze hard drives and smart phones. It has a plug-in architecture that allows you to find add-on modules or develop custom modules in Java or Python.

Autopsy Browser: https://www.autopsy.com/
Axiom Cyber: https://www.magnetforensics.com/products/magnet-axiom-cyber/
Browser History Examiner: https://www.foxtonforensics.com/
Browser History Examiner is a professional tool to investigate web browser activity

BlackLight: https://cellebrite.com/wp-content/uploads/2020/05/BlackBag_ProductOverview_blacklight.pdf
A market solution for the quick and comprehensive analysis of computer extractions. BlackLight® supports ongoing forensic toolkit integrations to bring into case one including products like Berla, Semantics 21, PhotoDNA ,Vic APOLLO Project and more.

Belkasoft Evidence Center: https://belkasoft.com/x
Bulk Extractor: https://github.com/simsong/bulk_extractor (conditions of the OpenSSL License and the original SSLeay license apply to the toolkit)
CAINE (Computer Aided INvestigative Environment): https://www.caine-live.net/
CAINE Live: http://www.caine-live.net/
CAINE (Computer Aided INvestigative Environment) is an Italian GNU/Linux live distribution created as a Digital Forensics project. Currently the project manager is Nanni Bassetti (Bari - Italy). CAINE offers a complete forensic environment that is organized to integrate existing software tools as software modules and to provide a friendly graphical interface. The main design objectives that CAINE aims to guarantee are the following: an interoperable environment that supports the digital investigator during the four phases of the digital investigation, a user-friendly graphical interface snd user-friendly tools
Cellebrite UFED: https://cellebrite.com/pt/inicio/

DC3DD: https://github.com/search?q=dc3dd&type=repositories
dc3dd is a patched version of GNU dd with added features for computer forensics: on the fly hashing (md5, sha-1, sha-256, and sha-512); possibility to write errors to a file; group errors in the error log; pattern wiping; progress report; possibility to split output.

dcfldd: https://github.com/resurrecting-open-source-projects/dcfldd (Open Source)
dcfldd is a modified version of GNU dd. dcfldd was originally created by Nicholas Harbour from the DoD Computer Forensics Laboratory (DCFL). Nick Harbour still maintaining the package, although he was no longer affiliated with the DCFL. Nowadays, dcfldd is maintained by volunteers.
DEFT (Digital Evidence & Forensic Toolkit): https://distrowatch.com/table.php?distribution=deft

Digital Forensics Framework (DFF): https://lnkd.in/dmzfPdSa
DFF (Digital Forensics Framework) is an Open Source computer forensics platform built on top of a dedicated Application Programming Interface (API). DFF proposes an alternative to the aging digital forensics solutions used today. Designed for simple use and automation, DFF interface guides the user through the main steps of a digital investigation so it can be used by both professional and non-expert to quickly and easily conduct a digital investigation and perform incident response.

Dumpzilla Forensic Tool: https://www.dumpzilla.org/
Dumpzilla application is developed in Python 3.x and has as purpose extract all forensic interesting information of Firefox, Iceweasel and Seamonkey browsers to be analyzed. Due to its Python 3.x developement, might not work properly in old Python versions, mainly with certain characters. Works under Unix and Windows 32/64 bits systems. Works in command line interface, so information dumps could be redirected by pipes with tools such as grep, awk, cut, sed... Dumpzilla allows to visualize following sections, search customization and extract certain content.

EnCase: https://www.opentext.com/products/encase-forensic
OpenText™ EnCase™ Forensic finds digital evidence no matter where it hides to help law enforcement and government agencies reduce case backlogs, close cases faster and improve public safety. For more than 20 years, investigators, attorneys and judges around the world have depended on EnCase Forensic as the pioneer in digital forensic software to deliver reliable investigation results.

EnCase Imager: https://www.opentext.com/products/tableau-tx1-forensic-imager
A versatile and intuitive forensic imaging solution that acquires data faster and from more media types, without sacrificing ease-of-use or portabilitySupport digital investigations with powerful, standalone forensic imaging and triage.

Excire Forensics: https://www.x-ways.net/
Photo analysis with artificial intelligence.

ExifTool by Phil Harvey- Read, Write and Edit Meta Information: https://exiftool.org/
ExifTool is a platform-independent Perl library plus a command-line application for reading, writing and editing meta information in a wide variety of files. ExifTool supports many different metadata formats including EXIF, GPS, IPTC, XMP, JFIF, GeoTIFF, ICC Profile, Photoshop IRB, FlashPix, AFCP and ID3, Lyrics3, as well as the maker notes of many digital cameras by Canon, Casio, DJI, FLIR, FujiFilm, GE, GoPro, HP, JVC/Victor, Kodak, Leaf, Minolta/Konica-Minolta, Motorola, Nikon, Nintendo, Olympus/Epson, Panasonic/Leica, Pentax/Asahi, Phase One, Reconyx, Ricoh, Samsung, Sanyo, Sigma/Foveon and Sony. ExifTool is also available as a stand-alone Windows executable and a MacOS package: (Note that these versions contain the executable only, and do not include the HTML documentation or other files of the full distribution.)

ExifTool Command Line: https://securiumsolutions.com/exiftool-meta-data-extractor-image-forensics-tool/
Exif-tool is a command-line interface to ExifTool, used for reading and writing meta information in image, audio and video files. We can review all hidden meta data on our given file, such as GPS, Meta-Data Information, information about captured camera along with time.

F-Response: https://www.x-ways.net/f-response.html
Remote network drive analysis capability, remote RAM access, cloud storage access, ...

Fibratus: https://github.com/rabbitstack/fibratus
Fibratus is a tool for exploration and tracing of the Windows kernel. It lets you trap system-wide events such as process life-cycle, file system I/O, registry modifications or network requests among many other observability signals. In a nutshell, Fibratus allows for gaining deep operational visibility into the Windows kernel but also processes running on top of it. It requires no drivers nor third-party software.


Forensic Email Collector: https://www.metaspike.com/fec-download-request/
Forensic Email Collector (FEC) is a desktop application that connects to email servers and forensically preserves mailboxes. You can download Forensic Email Collector through our DFIR Community or by requesting a download link to your email. Both options require that you be on our customer database. If you are not, please contact us with your order number

Ghiro: https://github.com/ghirensics/ghiro
Sometime forensic investigators need to process digital images as evidence. There are some tools around, otherwise it is difficult to deal with forensic analysis with lot of images involved. Images contain tons of information, Ghiro extracts these information from provided images and display them in a nicely formatted report. Dealing with tons of images is pretty easy, Ghiro is designed to scale to support gigs of images. All tasks are totally automated, you have just to upload you images and let Ghiro does the work. Understandable reports, and great search capabilities allows you to find a needle in a haystack. Ghiro is a multi user environment, different permissions can be assigned to each user. Cases allow you to group image analysis by topic, you can choose which user allow to see your case with a permission schema.

Guymager: https://github.com/gaurav-gogia/dftools/blob/master/guymager.md
A GUI forensic imaging/cloning tool that can either help by creating a forensic image of a drive or clone the drive instead. Just like DD/DC3DD this tool works by creating a bit-by-bit copy of the target. The tool supports file splitting(ideally E01 format/extension), reporting and hash calculatio

Hex Editor Neo: https://www.hhdsoftware.com/free-hex-editor
Free Hex Editor Neo is one of the top database forensics tools for handling large files. It is possible to modify large files with Free version of HHD Software Hex Editor Neo.

HxD: https://mh-nexus.de/en/hxd/license.php (Free Software - HxD Copyright© 2002-2020 by Maël Hörz)

TOOLS - iLEAPP: iOS Logs, Events, And Properties Parser
By Alexis Brignoni | Initialization vectors Blog | December 24, 2019
Introducing a Python 3 scripts that merges all abrignoni's previous iOS digital forensics and incident response scripts (DFIR) into one.

Intruder: https://www.openvas.org/
Intruder is one of the top cybersecurity auditing tools to use in 2021 for seeking weaknesses in systems before malicious cyberattacks. It is an online vulnerability scanner to find cybersecurity weaknesses in the digital infrastructure to avoid expensive data breaches. Tech companies can get access to servers, cloud systems, websites, as well as endpoint devices to scan with the industry-leading scanning engines. This cybersecurity auditing tool helps in seeking weaknesses including missing patches, misconfigurations, encryption weaknesses, and application bugs in unauthenticated areas. This audit tool provides automatic scanning while securing the evolving IT environment efficiently and effectively. Intruder offers services such as continuous vulnerability management, attack surface monitoring, effortless reporting and compliance, intelligent result as well as continuous penetration testing.

Kali Linux: https://www.kali.org/

Magnet AXIOM: https://www.magnetforensics.com/products/magnet-axiom/
Recover & Analyze Evidence in One Case. Examine digital evidence from mobile, cloud, computer, and vehicle sources, alongside third-party extractions all in one case file. Use powerful and intuitive analytical tools to automatically surface case-relevant evidence quickly.

Ngrep: https://github.com/jpr5/ngrep/
ngrep is like GNU grep applied to the network layer. It's a PCAP-based tool that allows you to specify an extended regular or hexadecimal expression to match against data payloads of packets. It understands many kinds of protocols, including IPv4/6, TCP, UDP, ICMPv4/6, IGMP and Raw, across a wide variety of interface types, and understands BPF filter logic in the same fashion as more common packet sniffing tools, such as tcpdump and snoop.
Tenable Nessus®: https://pt-br.tenable.com/products/nessus
Avaliação de vulnerabilidades. Avalia a superfície de ataque moderna além dos ativos de TI tradicionais: fortalece as aplicações Web, proteje sua infraestrutura da nuvem e provê visibilidade da sua superfície de ataque conectada à internet.
It provides high speed with in-depth assessments and free training. This audit tool is also helpful for educators, consultants, security practitioners, students, and working professionals to start their careers in cybersecurity. It provides utmost protection from future data breaches with unlimited assessments, configuration assessments, configurable reports, and on-demand training. Predictive Prioritization provides assistance in most critical cybersecurity issues with over 100 zero-day vulnerabilities.

NetworkMiner: https://www.netresec.com/?page=NetworkMiner (Open Source Digital Forensics)
NetworkMiner is an open source network forensics tool that extracts artifacts, such as files, images, emails and passwords, from captured network traffic in PCAP files. NetworkMiner can also be used to capture live network traffic by sniffing a network interface. Detailed information about each IP address in the analyzed network traffic is aggregated to a network host inventory, which can be used for passive asset discovery as well as to get an overview of which devices that are communicating. NetworkMiner is primarily designed to run in Windows, but can also be used in Linux. NetworkMiner has, since the first release in 2007, become a popular tool among incident response teams as well as law enforcement. NetworkMiner is today used by companies and organizations all over the world.

NMAP: https://nmap.org/
NMAP (Network Mapper) is a free Security Scanner. It is one of the cyber security forensics tools for network scanning and auditing. One of its core advantages is the fact that it supports almost every popular operating system in existence, including Windows, Linux, and Mac, including some less popular ones like Solaris and HP-UX.

OSSEC: https://stackshare.io/ossec
OSSEC is a free, open-source host-based intrusion detection system (HIDS) . It performs log analysis, integrity checking, registry monitoring, rootkit detection, time-based alerting, and active response. Ossec is a tool in the Security category of a tech stack.

OpenScap: https://www.open-scap.org/
Tools for managing system security and standards compliance. The OpenSCAP ecosystem provides multiple tools to assist administrators and auditors with assessment, measurement, and enforcement of security baselines. We maintain great flexibility and interoperability, reducing the costs of performing security audits.

OSForensics: https://www.osforensics.com/
An all-in-one digital forensic software designed to extract, decode, and analyze data. Extract data and artifacts from multiple devices with the capability for both mobile and computer forensic investigations.

Oxygen Forensic Detective: https://oxygenforensics.com/en/
An all-in-one digital forensic software designed to extract, decode, and analyze data. Extract data and artifacts from multiple devices with the capability for both mobile and computer forensic investigations.


PhotoRec: https://www.cgsecurity.org/wiki/PhotoRec
PhotoRec is file data recovery software designed to recover lost files including video, documents and archives from hard disks (Mechanical Hard drives, Solid State Drives...), CD-ROMs, and lost pictures (thus the Photo Recovery name) from digital camera memory. PhotoRec ignores the file system and goes after the underlying data, so it will still work even if your media's file system has been severely damaged or reformatted. PhotoRec is free - this open source multi-platform application is distributed under GNU General Public License (GPLV v2+). PhotoRec is a companion program to TestDisk, an application for recovering lost partitions on a wide variety of file systems and making non-bootable disks bootable again.

Paladin Recon-Itr: https://sumuri.com/software/paladin/
Solução de imagem, triagem e relatórios para macOS

Plaso (log2timeline): https://github.com/log2timeline/plaso
Plaso (Plaso Langar Að Safna Öllu), or super timeline all the things, is a Python-based engine used by several tools for automatic creation of timelines. Plaso default behavior is to create super timelines but it also supports creating more targeted timelines.

PyFlag: F.L.A.G Forensic and Log Analysis GUI: https://github.com/py4n6/pyflag
This application is designed to assist IT security professionals with analysing log files, tcpdump files and hard disk images for forensic evidence. PyFlag is designed to run on Linux and has been tested on recent versions of Redhat/Fedora and Debian (Stable/Testing). It performs data analyis using a mysql database. It is written in python and should be portable to other unix-like systems.
Redline: https://fireeye.market/apps/211364
Redline®, FireEye’s premier free endpoint security tool, provides host investigative capabilities to users to find signs of malicious activity through memory and file analysis and the development of a threat assessment profile. Use Redline to collect, analyze and filter endpoint data and perform IOC analysis and hit review. In addition, users of FireEye’s Endpoint Security (HX) can open triage collections directly in Redline for in-depth analysis, allowing the user to establish the timeline and scope of an incident. This app runs on Windows only.

RegRipper: https://github.com/keydet89/RegRipper3.0 (Open Source Digital Forensics under terms of the MIT License)
Scalpel: https://github.com/sleuthkit/scalpel (Apache 2.0 License)
Scalpel is a file carving and indexing application that runs on Linux and Windows. The first version of Scalpel, released in 2005, was based on Foremost 0.69. There have been a number of internal releases since the last public release, 1.60, primarily to support our own research.
SIFT (SANS Investigative Forensic Toolkit): https://www.sans.org/tools/sift-workstation/
The SIFT Workstation is a collection of free and open-source incident response and forensic tools designed to perform detailed digital forensic examinations in a variety of settings. It can match any current incident response and forensic tool suite. SIFT demonstrates that advanced incident response capabilities and deep-dive digital forensic techniques can be accomplished using cutting-edge open-source tools that are freely available and frequently updated.

Sleuth Kit: https://www.sleuthkit.org/ (Open Source Digital Forensics)
The Sleuth Kit® is a collection of command line tools and a C library that allows you to analyze disk images and recover files from them. It is used behind the scenes in Autopsy and many other open source and commercial forensics tools.

SolarWinds Network Configuration Manager: https://www.openvas.org/
SolarWinds Network Configuration Manager is used by multiple tech companies to incorporate high-level cybersecurity into the existing systems. It helps to reduce cost and save time to remain compliant with automated network configuration management and backup to eliminate data breaches from the future. It has some exciting and useful features such as vulnerability detection, network automation, configuration backup and restore, network inventory, and cyber auditing for compliance. This audit tool helps tech companies to see when a configuration in the network service path has changed, identify performance and configuration issues on key network devices, and accelerate troubleshooting for performance issues with its different products such as SolarWinds Network Performance Monitor, Network Insight for Cisco Nexus, Cisco ASA, Palo Alto Network devices, and PerfStack feature in the Orion Platform.

Snort: https://www.snort.org/ (Open Source)
Snort is the foremost Open Source Intrusion Prevention System (IPS) in the world. Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generates alerts for users. Snort can be deployed inline to stop these packets, as well. Snort has three primary uses: As a packet sniffer like tcpdump, as a packet logger — which is useful for network traffic debugging, or it can be used as a full-blown network intrusion prevention system. Snort can be downloaded and configured for personal and business use alike.>

Syxsense: https://www.syxsense.com/
Automated endpoint and vulnerability platform: visibility and control over the infrastructure. Reduce management burden and improve security at the same time.

Tcpdump: https://www.tcpdump.org/
tcpdump prints out a description of the contents of packets on a network interface that match the Boolean expression ; the description is preceded by a time stamp, printed, by default, as hours, minutes, seconds, and fractions of a second since midnight. It can also be run with the -w flag, which causes it to save the packet data to a file for later analysis, and/or with the -r flag, which causes it to read from a saved packet file rather than to read packets from a network interface. It can also be run with the -V flag, which causes it to read a list of saved packet files. In all cases, only packets that match expression will be processed by tcpdump

TekDefense Forensic Investigator: https://splunkbase.splunk.com/app/2895
The TekDefense Forensic Investigator app is designed to be a Splunk toolkit for the first responder. Most tools do not need Internet access with the exception of a couple which use API calls. This Splunk app provides free tools for the forensic investigator which include, but are not limited to the following: (1) VirusTotal Lookups; (2) Metascan Lookups; (3) Automater; (4) Base64 conversion; (5) XOR conversion; (6) HEX conversion; and more...

Toolsley: https://www.toolsley.com/
Toolsley is a privately owned website dedicated to bringing you no-hassle tools that just work!

TestDisk: https://www.cgsecurity.org/wiki/TestDisk
TestDisk is OpenSource software and is licensed under the terms of the GNU General Public License (GPL v2+). TestDisk is powerful free data recovery software! It was primarily designed to help recover lost partitions and/or make non-booting disks bootable again when these symptoms are caused by faulty software: certain types of viruses or human error (such as accidentally deleting a Partition Table). Partition table recovery using TestDisk is really easy. TestDisk can: (1) fix partition table, recover deleted partition; (2) recover FAT32 boot sector from its backup; (3) rebuild FAT12/FAT16/FAT32 boot sector; (4) fix FAT tables; Rebuild NTFS boot sector; (5) recover NTFS boot sector from its backup; and (6) fix MFT using MFT mirror

TSK (The Sleuth Kit): https://www.sleuthkit.org/sleuthkit/
The Sleuth Kit® (TSK) is a library and collection of command line tools that allow you to investigate disk images. The core functionality of TSK allows you to analyze volume and file system data. The library can be incorporated into larger digital forensics tools and the command line tools can be directly used to find evidence.

Volatility: https://www.volatilityfoundation.org/
The Volatility Foundation is an independent non-profit organization that maintains and promotes open source memory forensics with The Volatility Framework.

Volatility Framework: https://github.com/volatilityfoundation/volatility3
Wireshark: https://www.wireshark.org/
Wireshark is the world's foremost network protocol analyzer. It lets you see what's happening on your network at a microscopic level. It is the de facto (and often de jure) standard across many industries and educational institutions. Wireshark development thrives thanks to the contributions of networking experts across the globe. It is the continuation of a project that started in 1998.

WinHex: https://www.x-ways.net/winhex/
WinHex is in its core a universal hexadecimal editor, particularly helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security. An advanced tool for everyday and emergency use: inspect and edit all kinds of files, recover deleted files or lost data from hard drives with corrupt file systems or from digital camera cards. Features depend on the license type.

Wetstonetech Tools: https://www.wetstonetech.com/products/
Steganography and data diding. CSAM (child sexual abuse material) investigation. Malware discovery.

Xplico – Network Forensic Analysis Tool (NFAT): https://www.xplico.org/
The goal of Xplico is extract from an internet traffic capture the applications data contained. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico isn’t a network protocol analyzer. Xplico is an open source Network Forensic Analysis Tool (NFAT). Xplico is released under the GNU General Public License.

Xplico on GitHub
XRY (XAMN) – Mobile Forensics and Data Recovery Software: https://www.msab.com/product/xry-extract/
Retrieving the optimal forensic data is what matters. XRY recovers data fast, in a secure, efficient, and lawful manner. XRY Logical. XRY Physical. XRY Pro. XRY Photon. XRY Cloud. XRY PinPoint. XRY Camera.

X-Ways Forensics: https://www.x-ways.net/
Integrated computer forensics environment. Our flagship product, based on WinHex.

X-Ways Forensics: https://www.x-ways.net/
Disk imaging, disk cloning, virtual RAID reconstruction. Best speed, most intelligent compression.

X-Ways Investigator: https://www.x-ways.net/investigator/index-m.html
Reduced, simplified version of X-Ways Forensics for police investigators, lawyers, auditors, ...

WEBINÁRIOS


Webinar - Academia de Forense Digital
Por Daniel Avilla | Academia de Forense Digital| Março 2022
Apresentação de ferrramentas: Avila Forensics, Bytecode Viewer, Andriller, ...
PODCASTS


Podcast - FTK Mobile, Cellphone Forensics Tool Comparisons, and New Open Source Artifacts.
Competition is Heating Up in the Mobile Forensics Space.
By Heather Charpentier & Alexis "BRIGS" Brignoni | Digital Forensics Now | October 05, 2023

Podcast - How can DigitalL Evidence help solve crime?
By Heather Charpentier & Alexis "BRIGS" Brignoni | Magnet Forensics| October 05, 2023
Join investigators, examiners, and prosecutors as they share the riveting cases that helped define their careers and how digital forensics played a pivotal part in the investigation.

PADRÕES


NIST - Recommendation: Closed Circuit Television (CCTV) Digital Video Export Profile - Level 0 (Revision 1)
This document updates and replaces NISTIR 8161. This revised recommendation continues to focus on storing metadata to support video analytics. At the FBI's request, NIST conducted research and developed NISTIR 8161 as a recommendation to address the FBI's minimum interoperability requirements for the exporting and exchange of video recordings captured by closed circuit television (CCTV) digital video recording (DVR) systems. NIST termed these requirements "Level 0". Subsequently, NIST shared its findings and recommendations with video industry hardware and software manufacturers, and the relevant standards community.

IEC - IEC 62676-2-31:2019
Video surveillance systems for use in security applications - Part 2-31: Live streaming and control based on web services
This document defines procedures for communication between network video clients and video transmitter devices.

PROGRAMAS DE PESQUISA, DESENVOLVIMENTO E INOVAÇÃO


P&D - TITANIUM PROJECT - Tools for the Investigation of Transactions in Underground Markets.
TITANIUM has closed on 2020-04-30.

➼ Forensic Investigator
➼ Autopsy
➼ Dumpzilla
➼ Browser History
➼ FTK Imager<
➼ X-Ways Forensics
➼ CAINE
➼ Toolsley
➼ ExifTool
➼ Grapl
➼ Kali Linux
➼ KeePass
➼ Metasploit Framework
➼ Osquery
➼ OSSEC
➼ Panther
➼ Suricata
➼ Wazuh Cloud
➼ Zeek/Bro
Network security auditing tools
Audit tools are essential to protect business from malicious actions. The article explores some of the useful cybersecurity auditing tools (network security auditing tools) for identifying potential security risks and fix those efficiently and effectively.
➼ Intruder
➼ OpenVAS
➼ SolarWinds Network Configuration Manager
➼ Nessus
➼ Syxsense Manage
During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. This first set of tools mainly focused on computer forensics, although in recent years similar tools have evolved for the field of mobile device forensics.[1] This list includes notable examples of digital forensic tools.

TOOLS - Conheça 5 distros Linux para Pentest
By Staff | hackersec.com | September, 2021
5 distros usadas por hackers e profissionais de cibersegurança para pentest, engenharia reversa, forense, análise de malware, web hacking e entre outros.

TOOLS - Indexador e Processador de Evidências Digitais (IPED) / IPED Digital Forensic Tool
Por Coordenação Geral de Tecnologia da Informação (CGTI)/Serviço de Perícias em Informática (SEPINF) | DPF | 2022
Programa linha de comando em java originalmente desenvolvido pela para indexar relatórios do FTK 1.8 (convertidos pelo AsAP3) e relatórios do FTK 3+. Atualmente apresenta diversas funcionalidades presentes em softwares forenses comerciais, servindo como alternativa eficiente e de código aberto na maioria dos casos. Tem como objetivos: (1) facilitar a visualização de Laudos de extração de dados por parte da equipe de investigação e melhorar a qualidade de Laudos contendo resultados de pesquisas por palavraschave; e (2) facilitar a análise dos dados em soluções de SARD, como a descrita em Triagem de Mídias SETEC/DF. Foi desenvolvido pela Coordenação Geral de Tecnologia da Informação (CGTI) do Departamento de polícia Federal (DPF) do Brasil
IPED is an open source software that can be used to process and analyze digital evidence, often seized at crime scenes by law enforcement or in a corporate investigation by private examiners.
MANUAL

Repositório no github

TOOLS - OSINT-FORENSICS-MOBILE
From CScorza | Github |
During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. This first set of tools mainly focused on computer forensics, although in recent years similar tools have evolved for the field of mobile device forensics.[1] This list includes notable examples of digital forensic tools.



AccessData FTK Imager: https://www.exterro.com/ftk-imager
AccessData Forensic Toolkit (FTK): https://www.exterro.com/ftk-digital-forensics
Autopsy: https://www.sleuthkit.org/autopsy/
Autopsy® is an easy to use, GUI-based program that allows you to efficiently analyze hard drives and smart phones. It has a plug-in architecture that allows you to find add-on modules or develop custom modules in Java or Python.

Autopsy Browser: https://www.autopsy.com/
Axiom Cyber: https://www.magnetforensics.com/products/magnet-axiom-cyber/
Browser History Examiner: https://www.foxtonforensics.com/
Browser History Examiner is a professional tool to investigate web browser activity

BlackLight: https://cellebrite.com/wp-content/uploads/2020/05/BlackBag_ProductOverview_blacklight.pdf
A market solution for the quick and comprehensive analysis of computer extractions. BlackLight® supports ongoing forensic toolkit integrations to bring into case one including products like Berla, Semantics 21, PhotoDNA ,Vic APOLLO Project and more.

Belkasoft Evidence Center: https://belkasoft.com/x
Bulk Extractor: https://github.com/simsong/bulk_extractor (conditions of the OpenSSL License and the original SSLeay license apply to the toolkit)
CAINE (Computer Aided INvestigative Environment): https://www.caine-live.net/
CAINE Live: http://www.caine-live.net/
CAINE (Computer Aided INvestigative Environment) is an Italian GNU/Linux live distribution created as a Digital Forensics project. Currently the project manager is Nanni Bassetti (Bari - Italy). CAINE offers a complete forensic environment that is organized to integrate existing software tools as software modules and to provide a friendly graphical interface. The main design objectives that CAINE aims to guarantee are the following: an interoperable environment that supports the digital investigator during the four phases of the digital investigation, a user-friendly graphical interface snd user-friendly tools
Cellebrite UFED: https://cellebrite.com/pt/inicio/

DC3DD: https://github.com/search?q=dc3dd&type=repositories
dc3dd is a patched version of GNU dd with added features for computer forensics: on the fly hashing (md5, sha-1, sha-256, and sha-512); possibility to write errors to a file; group errors in the error log; pattern wiping; progress report; possibility to split output.

dcfldd: https://github.com/resurrecting-open-source-projects/dcfldd (Open Source)
dcfldd is a modified version of GNU dd. dcfldd was originally created by Nicholas Harbour from the DoD Computer Forensics Laboratory (DCFL). Nick Harbour still maintaining the package, although he was no longer affiliated with the DCFL. Nowadays, dcfldd is maintained by volunteers.

DEFT (Digital Evidence & Forensic Toolkit): https://distrowatch.com/table.php?distribution=deft

Digital Forensics Framework (DFF): https://lnkd.in/dmzfPdSa
DFF (Digital Forensics Framework) is an Open Source computer forensics platform built on top of a dedicated Application Programming Interface (API). DFF proposes an alternative to the aging digital forensics solutions used today. Designed for simple use and automation, DFF interface guides the user through the main steps of a digital investigation so it can be used by both professional and non-expert to quickly and easily conduct a digital investigation and perform incident response.

Dumpzilla Forensic Tool: https://www.dumpzilla.org/
Dumpzilla application is developed in Python 3.x and has as purpose extract all forensic interesting information of Firefox, Iceweasel and Seamonkey browsers to be analyzed. Due to its Python 3.x developement, might not work properly in old Python versions, mainly with certain characters. Works under Unix and Windows 32/64 bits systems. Works in command line interface, so information dumps could be redirected by pipes with tools such as grep, awk, cut, sed... Dumpzilla allows to visualize following sections, search customization and extract certain content.

EnCase: https://www.opentext.com/products/encase-forensic
OpenText™ EnCase™ Forensic finds digital evidence no matter where it hides to help law enforcement and government agencies reduce case backlogs, close cases faster and improve public safety. For more than 20 years, investigators, attorneys and judges around the world have depended on EnCase Forensic as the pioneer in digital forensic software to deliver reliable investigation results.

EnCase Imager: https://www.opentext.com/products/tableau-tx1-forensic-imager
A versatile and intuitive forensic imaging solution that acquires data faster and from more media types, without sacrificing ease-of-use or portabilitySupport digital investigations with powerful, standalone forensic imaging and triage.

Excire Forensics: https://www.x-ways.net/
Photo analysis with artificial intelligence.

ExifTool by Phil Harvey- Read, Write and Edit Meta Information: https://exiftool.org/
ExifTool is a platform-independent Perl library plus a command-line application for reading, writing and editing meta information in a wide variety of files. ExifTool supports many different metadata formats including EXIF, GPS, IPTC, XMP, JFIF, GeoTIFF, ICC Profile, Photoshop IRB, FlashPix, AFCP and ID3, Lyrics3, as well as the maker notes of many digital cameras by Canon, Casio, DJI, FLIR, FujiFilm, GE, GoPro, HP, JVC/Victor, Kodak, Leaf, Minolta/Konica-Minolta, Motorola, Nikon, Nintendo, Olympus/Epson, Panasonic/Leica, Pentax/Asahi, Phase One, Reconyx, Ricoh, Samsung, Sanyo, Sigma/Foveon and Sony. ExifTool is also available as a stand-alone Windows executable and a MacOS package: (Note that these versions contain the executable only, and do not include the HTML documentation or other files of the full distribution.)

ExifTool Command Line: https://securiumsolutions.com/exiftool-meta-data-extractor-image-forensics-tool/
Exif-tool is a command-line interface to ExifTool, used for reading and writing meta information in image, audio and video files. We can review all hidden meta data on our given file, such as GPS, Meta-Data Information, information about captured camera along with time.

F-Response: https://www.x-ways.net/f-response.html
Remote network drive analysis capability, remote RAM access, cloud storage access, ...

Fibratus: https://github.com/rabbitstack/fibratus
Fibratus is a tool for exploration and tracing of the Windows kernel. It lets you trap system-wide events such as process life-cycle, file system I/O, registry modifications or network requests among many other observability signals. In a nutshell, Fibratus allows for gaining deep operational visibility into the Windows kernel but also processes running on top of it. It requires no drivers nor third-party software.


Forensic Email Collector: https://www.metaspike.com/fec-download-request/
Forensic Email Collector (FEC) is a desktop application that connects to email servers and forensically preserves mailboxes. You can download Forensic Email Collector through our DFIR Community or by requesting a download link to your email. Both options require that you be on our customer database. If you are not, please contact us with your order number

Ghiro: https://github.com/ghirensics/ghiro
Sometime forensic investigators need to process digital images as evidence. There are some tools around, otherwise it is difficult to deal with forensic analysis with lot of images involved. Images contain tons of information, Ghiro extracts these information from provided images and display them in a nicely formatted report. Dealing with tons of images is pretty easy, Ghiro is designed to scale to support gigs of images. All tasks are totally automated, you have just to upload you images and let Ghiro does the work. Understandable reports, and great search capabilities allows you to find a needle in a haystack. Ghiro is a multi user environment, different permissions can be assigned to each user. Cases allow you to group image analysis by topic, you can choose which user allow to see your case with a permission schema.


Guymager: https://github.com/gaurav-gogia/dftools/blob/master/guymager.md
A GUI forensic imaging/cloning tool that can either help by creating a forensic image of a drive or clone the drive instead. Just like DD/DC3DD this tool works by creating a bit-by-bit copy of the target. The tool supports file splitting(ideally E01 format/extension), reporting and hash calculatio

Hex Editor Neo: https://www.hhdsoftware.com/free-hex-editor
Free Hex Editor Neo is one of the top database forensics tools for handling large files. It is possible to modify large files with Free version of HHD Software Hex Editor Neo.

HxD: https://mh-nexus.de/en/hxd/license.php (Free Software - HxD Copyright© 2002-2020 by Maël Hörz)

TOOLS - iLEAPP: iOS Logs, Events, And Properties Parser
By Alexis Brignoni | Initialization vectors Blog | December 24, 2019
Introducing a Python 3 scripts that merges all abrignoni's previous iOS digital forensics and incident response scripts (DFIR) into one.

Intruder: https://www.openvas.org/
Intruder is one of the top cybersecurity auditing tools to use in 2021 for seeking weaknesses in systems before malicious cyberattacks. It is an online vulnerability scanner to find cybersecurity weaknesses in the digital infrastructure to avoid expensive data breaches. Tech companies can get access to servers, cloud systems, websites, as well as endpoint devices to scan with the industry-leading scanning engines. This cybersecurity auditing tool helps in seeking weaknesses including missing patches, misconfigurations, encryption weaknesses, and application bugs in unauthenticated areas. This audit tool provides automatic scanning while securing the evolving IT environment efficiently and effectively. Intruder offers services such as continuous vulnerability management, attack surface monitoring, effortless reporting and compliance, intelligent result as well as continuous penetration testing.

Kali Linux: https://www.kali.org/

Magnet AXIOM: https://www.magnetforensics.com/products/magnet-axiom/
Recover & Analyze Evidence in One Case. Examine digital evidence from mobile, cloud, computer, and vehicle sources, alongside third-party extractions all in one case file. Use powerful and intuitive analytical tools to automatically surface case-relevant evidence quickly.

Ngrep: https://github.com/jpr5/ngrep/
ngrep is like GNU grep applied to the network layer. It's a PCAP-based tool that allows you to specify an extended regular or hexadecimal expression to match against data payloads of packets. It understands many kinds of protocols, including IPv4/6, TCP, UDP, ICMPv4/6, IGMP and Raw, across a wide variety of interface types, and understands BPF filter logic in the same fashion as more common packet sniffing tools, such as tcpdump and snoop.

Tenable Nessus®: https://pt-br.tenable.com/products/nessus
Avaliação de vulnerabilidades. Avalia a superfície de ataque moderna além dos ativos de TI tradicionais: fortalece as aplicações Web, proteje sua infraestrutura da nuvem e provê visibilidade da sua superfície de ataque conectada à internet.
It provides high speed with in-depth assessments and free training. This audit tool is also helpful for educators, consultants, security practitioners, students, and working professionals to start their careers in cybersecurity. It provides utmost protection from future data breaches with unlimited assessments, configuration assessments, configurable reports, and on-demand training. Predictive Prioritization provides assistance in most critical cybersecurity issues with over 100 zero-day vulnerabilities.

NetworkMiner: https://www.netresec.com/?page=NetworkMiner (Open Source Digital Forensics)
NetworkMiner is an open source network forensics tool that extracts artifacts, such as files, images, emails and passwords, from captured network traffic in PCAP files. NetworkMiner can also be used to capture live network traffic by sniffing a network interface. Detailed information about each IP address in the analyzed network traffic is aggregated to a network host inventory, which can be used for passive asset discovery as well as to get an overview of which devices that are communicating. NetworkMiner is primarily designed to run in Windows, but can also be used in Linux. NetworkMiner has, since the first release in 2007, become a popular tool among incident response teams as well as law enforcement. NetworkMiner is today used by companies and organizations all over the world.

NMAP: https://nmap.org/
NMAP (Network Mapper) is a free Security Scanner. It is one of the cyber security forensics tools for network scanning and auditing. One of its core advantages is the fact that it supports almost every popular operating system in existence, including Windows, Linux, and Mac, including some less popular ones like Solaris and HP-UX.

OSSEC: https://stackshare.io/ossec
OSSEC is a free, open-source host-based intrusion detection system (HIDS) . It performs log analysis, integrity checking, registry monitoring, rootkit detection, time-based alerting, and active response. Ossec is a tool in the Security category of a tech stack.

OpenScap: https://www.open-scap.org/
Tools for managing system security and standards compliance. The OpenSCAP ecosystem provides multiple tools to assist administrators and auditors with assessment, measurement, and enforcement of security baselines. We maintain great flexibility and interoperability, reducing the costs of performing security audits.

OSForensics: https://www.osforensics.com/
An all-in-one digital forensic software designed to extract, decode, and analyze data. Extract data and artifacts from multiple devices with the capability for both mobile and computer forensic investigations.

Oxygen Forensic Detective: https://oxygenforensics.com/en/
An all-in-one digital forensic software designed to extract, decode, and analyze data. Extract data and artifacts from multiple devices with the capability for both mobile and computer forensic investigations.


PhotoRec: https://www.cgsecurity.org/wiki/PhotoRec
PhotoRec is file data recovery software designed to recover lost files including video, documents and archives from hard disks (Mechanical Hard drives, Solid State Drives...), CD-ROMs, and lost pictures (thus the Photo Recovery name) from digital camera memory. PhotoRec ignores the file system and goes after the underlying data, so it will still work even if your media's file system has been severely damaged or reformatted. PhotoRec is free - this open source multi-platform application is distributed under GNU General Public License (GPLV v2+). PhotoRec is a companion program to TestDisk, an application for recovering lost partitions on a wide variety of file systems and making non-bootable disks bootable again.

Paladin Recon-Itr: https://sumuri.com/software/paladin/
Solução de imagem, triagem e relatórios para macOS

Plaso (log2timeline): https://github.com/log2timeline/plaso
Plaso (Plaso Langar Að Safna Öllu), or super timeline all the things, is a Python-based engine used by several tools for automatic creation of timelines. Plaso default behavior is to create super timelines but it also supports creating more targeted timelines.

PyFlag: F.L.A.G Forensic and Log Analysis GUI: https://github.com/py4n6/pyflag
This application is designed to assist IT security professionals with analysing log files, tcpdump files and hard disk images for forensic evidence. PyFlag is designed to run on Linux and has been tested on recent versions of Redhat/Fedora and Debian (Stable/Testing). It performs data analyis using a mysql database. It is written in python and should be portable to other unix-like systems.

Redline: https://fireeye.market/apps/211364
Redline®, FireEye’s premier free endpoint security tool, provides host investigative capabilities to users to find signs of malicious activity through memory and file analysis and the development of a threat assessment profile. Use Redline to collect, analyze and filter endpoint data and perform IOC analysis and hit review. In addition, users of FireEye’s Endpoint Security (HX) can open triage collections directly in Redline for in-depth analysis, allowing the user to establish the timeline and scope of an incident. This app runs on Windows only.

RegRipper: https://github.com/keydet89/RegRipper3.0 (Open Source Digital Forensics under terms of the MIT License)

Scalpel: https://github.com/sleuthkit/scalpel (Apache 2.0 License)
Scalpel is a file carving and indexing application that runs on Linux and Windows. The first version of Scalpel, released in 2005, was based on Foremost 0.69. There have been a number of internal releases since the last public release, 1.60, primarily to support our own research.

SIFT (SANS Investigative Forensic Toolkit): https://www.sans.org/tools/sift-workstation/
The SIFT Workstation is a collection of free and open-source incident response and forensic tools designed to perform detailed digital forensic examinations in a variety of settings. It can match any current incident response and forensic tool suite. SIFT demonstrates that advanced incident response capabilities and deep-dive digital forensic techniques can be accomplished using cutting-edge open-source tools that are freely available and frequently updated.

Sleuth Kit: https://www.sleuthkit.org/ (Open Source Digital Forensics)
The Sleuth Kit® is a collection of command line tools and a C library that allows you to analyze disk images and recover files from them. It is used behind the scenes in Autopsy and many other open source and commercial forensics tools.

SolarWinds Network Configuration Manager: https://www.openvas.org/
SolarWinds Network Configuration Manager is used by multiple tech companies to incorporate high-level cybersecurity into the existing systems. It helps to reduce cost and save time to remain compliant with automated network configuration management and backup to eliminate data breaches from the future. It has some exciting and useful features such as vulnerability detection, network automation, configuration backup and restore, network inventory, and cyber auditing for compliance. This audit tool helps tech companies to see when a configuration in the network service path has changed, identify performance and configuration issues on key network devices, and accelerate troubleshooting for performance issues with its different products such as SolarWinds Network Performance Monitor, Network Insight for Cisco Nexus, Cisco ASA, Palo Alto Network devices, and PerfStack feature in the Orion Platform.

Snort: https://www.snort.org/ (Open Source)
Snort is the foremost Open Source Intrusion Prevention System (IPS) in the world. Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generates alerts for users. Snort can be deployed inline to stop these packets, as well. Snort has three primary uses: As a packet sniffer like tcpdump, as a packet logger — which is useful for network traffic debugging, or it can be used as a full-blown network intrusion prevention system. Snort can be downloaded and configured for personal and business use alike.>

Syxsense: https://www.syxsense.com/
Automated endpoint and vulnerability platform: visibility and control over the infrastructure. Reduce management burden and improve security at the same time.

Tcpdump: https://www.tcpdump.org/
tcpdump prints out a description of the contents of packets on a network interface that match the Boolean expression ; the description is preceded by a time stamp, printed, by default, as hours, minutes, seconds, and fractions of a second since midnight. It can also be run with the -w flag, which causes it to save the packet data to a file for later analysis, and/or with the -r flag, which causes it to read from a saved packet file rather than to read packets from a network interface. It can also be run with the -V flag, which causes it to read a list of saved packet files. In all cases, only packets that match expression will be processed by tcpdump

TekDefense Forensic Investigator: https://splunkbase.splunk.com/app/2895
The TekDefense Forensic Investigator app is designed to be a Splunk toolkit for the first responder. Most tools do not need Internet access with the exception of a couple which use API calls. This Splunk app provides free tools for the forensic investigator which include, but are not limited to the following: (1) VirusTotal Lookups; (2) Metascan Lookups; (3) Automater; (4) Base64 conversion; (5) XOR conversion; (6) HEX conversion; and more...

Toolsley: https://www.toolsley.com/
Toolsley is a privately owned website dedicated to bringing you no-hassle tools that just work!

TestDisk: https://www.cgsecurity.org/wiki/TestDisk
TestDisk is OpenSource software and is licensed under the terms of the GNU General Public License (GPL v2+). TestDisk is powerful free data recovery software! It was primarily designed to help recover lost partitions and/or make non-booting disks bootable again when these symptoms are caused by faulty software: certain types of viruses or human error (such as accidentally deleting a Partition Table). Partition table recovery using TestDisk is really easy. TestDisk can: (1) fix partition table, recover deleted partition; (2) recover FAT32 boot sector from its backup; (3) rebuild FAT12/FAT16/FAT32 boot sector; (4) fix FAT tables; Rebuild NTFS boot sector; (5) recover NTFS boot sector from its backup; and (6) fix MFT using MFT mirror

TSK (The Sleuth Kit): https://www.sleuthkit.org/sleuthkit/
The Sleuth Kit® (TSK) is a library and collection of command line tools that allow you to investigate disk images. The core functionality of TSK allows you to analyze volume and file system data. The library can be incorporated into larger digital forensics tools and the command line tools can be directly used to find evidence.

Volatility: https://www.volatilityfoundation.org/
The Volatility Foundation is an independent non-profit organization that maintains and promotes open source memory forensics with The Volatility Framework.
Programa linha de comando em java originalmente desenvolvido pela para indexar relatórios do FTK 1.8 (convertidos pelo AsAP3) e relatórios do FTK 3+. Atualmente apresenta diversas funcionalidades presentes em softwares forenses comerciais, servindo como alternativa eficiente e de código aberto na maioria dos casos. Tem como objetivos: (1) facilitar a visualização de Laudos de extração de dados por parte da equipe de investigação e melhorar a qualidade de Laudos contendo resultados de pesquisas por palavraschave; e (2) facilitar a análise dos dados em soluções de SARD, como a descrita em Triagem de Mídias SETEC/DF. Foi desenvolvido pela Coordenação Geral de Tecnologia da Informação (CGTI) do Departamento de polícia Federal (DPF) do Brasil
IPED is an open source software that can be used to process and analyze digital evidence, often seized at crime scenes by law enforcement or in a corporate investigation by private examiners.
MANUAL

Repositório no github

TOOLS - OSINT-FORENSICS-MOBILE
From CScorza | Github |
During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. This first set of tools mainly focused on computer forensics, although in recent years similar tools have evolved for the field of mobile device forensics.[1] This list includes notable examples of digital forensic tools.



AccessData FTK Imager: https://www.exterro.com/ftk-imager
AccessData Forensic Toolkit (FTK): https://www.exterro.com/ftk-digital-forensics
Autopsy: https://www.sleuthkit.org/autopsy/
Autopsy® is an easy to use, GUI-based program that allows you to efficiently analyze hard drives and smart phones. It has a plug-in architecture that allows you to find add-on modules or develop custom modules in Java or Python.

Autopsy Browser: https://www.autopsy.com/
Axiom Cyber: https://www.magnetforensics.com/products/magnet-axiom-cyber/
Browser History Examiner: https://www.foxtonforensics.com/
Browser History Examiner is a professional tool to investigate web browser activity

BlackLight: https://cellebrite.com/wp-content/uploads/2020/05/BlackBag_ProductOverview_blacklight.pdf
A market solution for the quick and comprehensive analysis of computer extractions. BlackLight® supports ongoing forensic toolkit integrations to bring into case one including products like Berla, Semantics 21, PhotoDNA ,Vic APOLLO Project and more.

Belkasoft Evidence Center: https://belkasoft.com/x
Bulk Extractor: https://github.com/simsong/bulk_extractor (conditions of the OpenSSL License and the original SSLeay license apply to the toolkit)
CAINE (Computer Aided INvestigative Environment): https://www.caine-live.net/
CAINE Live: http://www.caine-live.net/
CAINE (Computer Aided INvestigative Environment) is an Italian GNU/Linux live distribution created as a Digital Forensics project. Currently the project manager is Nanni Bassetti (Bari - Italy). CAINE offers a complete forensic environment that is organized to integrate existing software tools as software modules and to provide a friendly graphical interface. The main design objectives that CAINE aims to guarantee are the following: an interoperable environment that supports the digital investigator during the four phases of the digital investigation, a user-friendly graphical interface snd user-friendly tools
Cellebrite UFED: https://cellebrite.com/pt/inicio/

DC3DD: https://github.com/search?q=dc3dd&type=repositories
dc3dd is a patched version of GNU dd with added features for computer forensics: on the fly hashing (md5, sha-1, sha-256, and sha-512); possibility to write errors to a file; group errors in the error log; pattern wiping; progress report; possibility to split output.

dcfldd: https://github.com/resurrecting-open-source-projects/dcfldd (Open Source)
dcfldd is a modified version of GNU dd. dcfldd was originally created by Nicholas Harbour from the DoD Computer Forensics Laboratory (DCFL). Nick Harbour still maintaining the package, although he was no longer affiliated with the DCFL. Nowadays, dcfldd is maintained by volunteers.

DEFT (Digital Evidence & Forensic Toolkit): https://distrowatch.com/table.php?distribution=deft

Digital Forensics Framework (DFF): https://lnkd.in/dmzfPdSa
DFF (Digital Forensics Framework) is an Open Source computer forensics platform built on top of a dedicated Application Programming Interface (API). DFF proposes an alternative to the aging digital forensics solutions used today. Designed for simple use and automation, DFF interface guides the user through the main steps of a digital investigation so it can be used by both professional and non-expert to quickly and easily conduct a digital investigation and perform incident response.

Dumpzilla Forensic Tool: https://www.dumpzilla.org/
Dumpzilla application is developed in Python 3.x and has as purpose extract all forensic interesting information of Firefox, Iceweasel and Seamonkey browsers to be analyzed. Due to its Python 3.x developement, might not work properly in old Python versions, mainly with certain characters. Works under Unix and Windows 32/64 bits systems. Works in command line interface, so information dumps could be redirected by pipes with tools such as grep, awk, cut, sed... Dumpzilla allows to visualize following sections, search customization and extract certain content.

EnCase: https://www.opentext.com/products/encase-forensic
OpenText™ EnCase™ Forensic finds digital evidence no matter where it hides to help law enforcement and government agencies reduce case backlogs, close cases faster and improve public safety. For more than 20 years, investigators, attorneys and judges around the world have depended on EnCase Forensic as the pioneer in digital forensic software to deliver reliable investigation results.

EnCase Imager: https://www.opentext.com/products/tableau-tx1-forensic-imager
A versatile and intuitive forensic imaging solution that acquires data faster and from more media types, without sacrificing ease-of-use or portabilitySupport digital investigations with powerful, standalone forensic imaging and triage.

Excire Forensics: https://www.x-ways.net/
Photo analysis with artificial intelligence.

ExifTool by Phil Harvey- Read, Write and Edit Meta Information: https://exiftool.org/
ExifTool is a platform-independent Perl library plus a command-line application for reading, writing and editing meta information in a wide variety of files. ExifTool supports many different metadata formats including EXIF, GPS, IPTC, XMP, JFIF, GeoTIFF, ICC Profile, Photoshop IRB, FlashPix, AFCP and ID3, Lyrics3, as well as the maker notes of many digital cameras by Canon, Casio, DJI, FLIR, FujiFilm, GE, GoPro, HP, JVC/Victor, Kodak, Leaf, Minolta/Konica-Minolta, Motorola, Nikon, Nintendo, Olympus/Epson, Panasonic/Leica, Pentax/Asahi, Phase One, Reconyx, Ricoh, Samsung, Sanyo, Sigma/Foveon and Sony. ExifTool is also available as a stand-alone Windows executable and a MacOS package: (Note that these versions contain the executable only, and do not include the HTML documentation or other files of the full distribution.)

ExifTool Command Line: https://securiumsolutions.com/exiftool-meta-data-extractor-image-forensics-tool/
Exif-tool is a command-line interface to ExifTool, used for reading and writing meta information in image, audio and video files. We can review all hidden meta data on our given file, such as GPS, Meta-Data Information, information about captured camera along with time.

F-Response: https://www.x-ways.net/f-response.html
Remote network drive analysis capability, remote RAM access, cloud storage access, ...

Fibratus: https://github.com/rabbitstack/fibratus
Fibratus is a tool for exploration and tracing of the Windows kernel. It lets you trap system-wide events such as process life-cycle, file system I/O, registry modifications or network requests among many other observability signals. In a nutshell, Fibratus allows for gaining deep operational visibility into the Windows kernel but also processes running on top of it. It requires no drivers nor third-party software.


Forensic Email Collector: https://www.metaspike.com/fec-download-request/
Forensic Email Collector (FEC) is a desktop application that connects to email servers and forensically preserves mailboxes. You can download Forensic Email Collector through our DFIR Community or by requesting a download link to your email. Both options require that you be on our customer database. If you are not, please contact us with your order number

Ghiro: https://github.com/ghirensics/ghiro
Sometime forensic investigators need to process digital images as evidence. There are some tools around, otherwise it is difficult to deal with forensic analysis with lot of images involved. Images contain tons of information, Ghiro extracts these information from provided images and display them in a nicely formatted report. Dealing with tons of images is pretty easy, Ghiro is designed to scale to support gigs of images. All tasks are totally automated, you have just to upload you images and let Ghiro does the work. Understandable reports, and great search capabilities allows you to find a needle in a haystack. Ghiro is a multi user environment, different permissions can be assigned to each user. Cases allow you to group image analysis by topic, you can choose which user allow to see your case with a permission schema.


Guymager: https://github.com/gaurav-gogia/dftools/blob/master/guymager.md
A GUI forensic imaging/cloning tool that can either help by creating a forensic image of a drive or clone the drive instead. Just like DD/DC3DD this tool works by creating a bit-by-bit copy of the target. The tool supports file splitting(ideally E01 format/extension), reporting and hash calculatio

Hex Editor Neo: https://www.hhdsoftware.com/free-hex-editor
Free Hex Editor Neo is one of the top database forensics tools for handling large files. It is possible to modify large files with Free version of HHD Software Hex Editor Neo.

HxD: https://mh-nexus.de/en/hxd/license.php (Free Software - HxD Copyright© 2002-2020 by Maël Hörz)

TOOLS - iLEAPP: iOS Logs, Events, And Properties Parser
By Alexis Brignoni | Initialization vectors Blog | December 24, 2019
Introducing a Python 3 scripts that merges all abrignoni's previous iOS digital forensics and incident response scripts (DFIR) into one.

Intruder: https://www.openvas.org/
Intruder is one of the top cybersecurity auditing tools to use in 2021 for seeking weaknesses in systems before malicious cyberattacks. It is an online vulnerability scanner to find cybersecurity weaknesses in the digital infrastructure to avoid expensive data breaches. Tech companies can get access to servers, cloud systems, websites, as well as endpoint devices to scan with the industry-leading scanning engines. This cybersecurity auditing tool helps in seeking weaknesses including missing patches, misconfigurations, encryption weaknesses, and application bugs in unauthenticated areas. This audit tool provides automatic scanning while securing the evolving IT environment efficiently and effectively. Intruder offers services such as continuous vulnerability management, attack surface monitoring, effortless reporting and compliance, intelligent result as well as continuous penetration testing.

Kali Linux: https://www.kali.org/

Magnet AXIOM: https://www.magnetforensics.com/products/magnet-axiom/
Recover & Analyze Evidence in One Case. Examine digital evidence from mobile, cloud, computer, and vehicle sources, alongside third-party extractions all in one case file. Use powerful and intuitive analytical tools to automatically surface case-relevant evidence quickly.

Ngrep: https://github.com/jpr5/ngrep/
ngrep is like GNU grep applied to the network layer. It's a PCAP-based tool that allows you to specify an extended regular or hexadecimal expression to match against data payloads of packets. It understands many kinds of protocols, including IPv4/6, TCP, UDP, ICMPv4/6, IGMP and Raw, across a wide variety of interface types, and understands BPF filter logic in the same fashion as more common packet sniffing tools, such as tcpdump and snoop.

During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. This first set of tools mainly focused on computer forensics, although in recent years similar tools have evolved for the field of mobile device forensics.[1] This list includes notable examples of digital forensic tools.



AccessData FTK Imager: https://www.exterro.com/ftk-imager
AccessData Forensic Toolkit (FTK): https://www.exterro.com/ftk-digital-forensics
Autopsy: https://www.sleuthkit.org/autopsy/
Autopsy® is an easy to use, GUI-based program that allows you to efficiently analyze hard drives and smart phones. It has a plug-in architecture that allows you to find add-on modules or develop custom modules in Java or Python.

Autopsy Browser: https://www.autopsy.com/
Axiom Cyber: https://www.magnetforensics.com/products/magnet-axiom-cyber/
Browser History Examiner: https://www.foxtonforensics.com/
Browser History Examiner is a professional tool to investigate web browser activity

BlackLight: https://cellebrite.com/wp-content/uploads/2020/05/BlackBag_ProductOverview_blacklight.pdf
A market solution for the quick and comprehensive analysis of computer extractions. BlackLight® supports ongoing forensic toolkit integrations to bring into case one including products like Berla, Semantics 21, PhotoDNA ,Vic APOLLO Project and more.

Belkasoft Evidence Center: https://belkasoft.com/x
Bulk Extractor: https://github.com/simsong/bulk_extractor (conditions of the OpenSSL License and the original SSLeay license apply to the toolkit)
CAINE (Computer Aided INvestigative Environment): https://www.caine-live.net/
CAINE Live: http://www.caine-live.net/
CAINE (Computer Aided INvestigative Environment) is an Italian GNU/Linux live distribution created as a Digital Forensics project. Currently the project manager is Nanni Bassetti (Bari - Italy). CAINE offers a complete forensic environment that is organized to integrate existing software tools as software modules and to provide a friendly graphical interface. The main design objectives that CAINE aims to guarantee are the following: an interoperable environment that supports the digital investigator during the four phases of the digital investigation, a user-friendly graphical interface snd user-friendly tools
Cellebrite UFED: https://cellebrite.com/pt/inicio/

DC3DD: https://github.com/search?q=dc3dd&type=repositories
dc3dd is a patched version of GNU dd with added features for computer forensics: on the fly hashing (md5, sha-1, sha-256, and sha-512); possibility to write errors to a file; group errors in the error log; pattern wiping; progress report; possibility to split output.
dcfldd: https://github.com/resurrecting-open-source-projects/dcfldd (Open Source)
dcfldd is a modified version of GNU dd. dcfldd was originally created by Nicholas Harbour from the DoD Computer Forensics Laboratory (DCFL). Nick Harbour still maintaining the package, although he was no longer affiliated with the DCFL. Nowadays, dcfldd is maintained by volunteers.

DEFT (Digital Evidence & Forensic Toolkit): https://distrowatch.com/table.php?distribution=deft

Digital Forensics Framework (DFF): https://lnkd.in/dmzfPdSa
DFF (Digital Forensics Framework) is an Open Source computer forensics platform built on top of a dedicated Application Programming Interface (API). DFF proposes an alternative to the aging digital forensics solutions used today. Designed for simple use and automation, DFF interface guides the user through the main steps of a digital investigation so it can be used by both professional and non-expert to quickly and easily conduct a digital investigation and perform incident response.

Dumpzilla Forensic Tool: https://www.dumpzilla.org/
Dumpzilla application is developed in Python 3.x and has as purpose extract all forensic interesting information of Firefox, Iceweasel and Seamonkey browsers to be analyzed. Due to its Python 3.x developement, might not work properly in old Python versions, mainly with certain characters. Works under Unix and Windows 32/64 bits systems. Works in command line interface, so information dumps could be redirected by pipes with tools such as grep, awk, cut, sed... Dumpzilla allows to visualize following sections, search customization and extract certain content.

EnCase: https://www.opentext.com/products/encase-forensic
OpenText™ EnCase™ Forensic finds digital evidence no matter where it hides to help law enforcement and government agencies reduce case backlogs, close cases faster and improve public safety. For more than 20 years, investigators, attorneys and judges around the world have depended on EnCase Forensic as the pioneer in digital forensic software to deliver reliable investigation results.

EnCase Imager: https://www.opentext.com/products/tableau-tx1-forensic-imager
A versatile and intuitive forensic imaging solution that acquires data faster and from more media types, without sacrificing ease-of-use or portabilitySupport digital investigations with powerful, standalone forensic imaging and triage.

Excire Forensics: https://www.x-ways.net/
Photo analysis with artificial intelligence.
ExifTool by Phil Harvey- Read, Write and Edit Meta Information: https://exiftool.org/
ExifTool is a platform-independent Perl library plus a command-line application for reading, writing and editing meta information in a wide variety of files. ExifTool supports many different metadata formats including EXIF, GPS, IPTC, XMP, JFIF, GeoTIFF, ICC Profile, Photoshop IRB, FlashPix, AFCP and ID3, Lyrics3, as well as the maker notes of many digital cameras by Canon, Casio, DJI, FLIR, FujiFilm, GE, GoPro, HP, JVC/Victor, Kodak, Leaf, Minolta/Konica-Minolta, Motorola, Nikon, Nintendo, Olympus/Epson, Panasonic/Leica, Pentax/Asahi, Phase One, Reconyx, Ricoh, Samsung, Sanyo, Sigma/Foveon and Sony. ExifTool is also available as a stand-alone Windows executable and a MacOS package: (Note that these versions contain the executable only, and do not include the HTML documentation or other files of the full distribution.)

ExifTool Command Line: https://securiumsolutions.com/exiftool-meta-data-extractor-image-forensics-tool/
Exif-tool is a command-line interface to ExifTool, used for reading and writing meta information in image, audio and video files. We can review all hidden meta data on our given file, such as GPS, Meta-Data Information, information about captured camera along with time.

F-Response: https://www.x-ways.net/f-response.html
Remote network drive analysis capability, remote RAM access, cloud storage access, ...

Fibratus: https://github.com/rabbitstack/fibratus
Fibratus is a tool for exploration and tracing of the Windows kernel. It lets you trap system-wide events such as process life-cycle, file system I/O, registry modifications or network requests among many other observability signals. In a nutshell, Fibratus allows for gaining deep operational visibility into the Windows kernel but also processes running on top of it. It requires no drivers nor third-party software.


Forensic Email Collector: https://www.metaspike.com/fec-download-request/
Forensic Email Collector (FEC) is a desktop application that connects to email servers and forensically preserves mailboxes. You can download Forensic Email Collector through our DFIR Community or by requesting a download link to your email. Both options require that you be on our customer database. If you are not, please contact us with your order number

Ghiro: https://github.com/ghirensics/ghiro
Sometime forensic investigators need to process digital images as evidence. There are some tools around, otherwise it is difficult to deal with forensic analysis with lot of images involved. Images contain tons of information, Ghiro extracts these information from provided images and display them in a nicely formatted report. Dealing with tons of images is pretty easy, Ghiro is designed to scale to support gigs of images. All tasks are totally automated, you have just to upload you images and let Ghiro does the work. Understandable reports, and great search capabilities allows you to find a needle in a haystack. Ghiro is a multi user environment, different permissions can be assigned to each user. Cases allow you to group image analysis by topic, you can choose which user allow to see your case with a permission schema.


Guymager: https://github.com/gaurav-gogia/dftools/blob/master/guymager.md
A GUI forensic imaging/cloning tool that can either help by creating a forensic image of a drive or clone the drive instead. Just like DD/DC3DD this tool works by creating a bit-by-bit copy of the target. The tool supports file splitting(ideally E01 format/extension), reporting and hash calculatio

Hex Editor Neo: https://www.hhdsoftware.com/free-hex-editor
Free Hex Editor Neo is one of the top database forensics tools for handling large files. It is possible to modify large files with Free version of HHD Software Hex Editor Neo.
HxD: https://mh-nexus.de/en/hxd/license.php (Free Software - HxD Copyright© 2002-2020 by Maël Hörz)

TOOLS - iLEAPP: iOS Logs, Events, And Properties Parser
By Alexis Brignoni | Initialization vectors Blog | December 24, 2019
Introducing a Python 3 scripts that merges all abrignoni's previous iOS digital forensics and incident response scripts (DFIR) into one.

Intruder: https://www.openvas.org/
Intruder is one of the top cybersecurity auditing tools to use in 2021 for seeking weaknesses in systems before malicious cyberattacks. It is an online vulnerability scanner to find cybersecurity weaknesses in the digital infrastructure to avoid expensive data breaches. Tech companies can get access to servers, cloud systems, websites, as well as endpoint devices to scan with the industry-leading scanning engines. This cybersecurity auditing tool helps in seeking weaknesses including missing patches, misconfigurations, encryption weaknesses, and application bugs in unauthenticated areas. This audit tool provides automatic scanning while securing the evolving IT environment efficiently and effectively. Intruder offers services such as continuous vulnerability management, attack surface monitoring, effortless reporting and compliance, intelligent result as well as continuous penetration testing.

Kali Linux: https://www.kali.org/

Magnet AXIOM: https://www.magnetforensics.com/products/magnet-axiom/
Recover & Analyze Evidence in One Case. Examine digital evidence from mobile, cloud, computer, and vehicle sources, alongside third-party extractions all in one case file. Use powerful and intuitive analytical tools to automatically surface case-relevant evidence quickly.
It provides high speed with in-depth assessments and free training. This audit tool is also helpful for educators, consultants, security practitioners, students, and working professionals to start their careers in cybersecurity. It provides utmost protection from future data breaches with unlimited assessments, configuration assessments, configurable reports, and on-demand training. Predictive Prioritization provides assistance in most critical cybersecurity issues with over 100 zero-day vulnerabilities.

Volatility Framework: https://github.com/volatilityfoundation/volatility3

Wireshark: https://www.wireshark.org/
Wireshark is the world's foremost network protocol analyzer. It lets you see what's happening on your network at a microscopic level. It is the de facto (and often de jure) standard across many industries and educational institutions. Wireshark development thrives thanks to the contributions of networking experts across the globe. It is the continuation of a project that started in 1998.

WinHex: https://www.x-ways.net/winhex/
WinHex is in its core a universal hexadecimal editor, particularly helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security. An advanced tool for everyday and emergency use: inspect and edit all kinds of files, recover deleted files or lost data from hard drives with corrupt file systems or from digital camera cards. Features depend on the license type.

Wetstonetech Tools: https://www.wetstonetech.com/products/
Steganography and data diding. CSAM (child sexual abuse material) investigation. Malware discovery.

Xplico – Network Forensic Analysis Tool (NFAT): https://www.xplico.org/
The goal of Xplico is extract from an internet traffic capture the applications data contained. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico isn’t a network protocol analyzer. Xplico is an open source Network Forensic Analysis Tool (NFAT). Xplico is released under the GNU General Public License.

Xplico on GitHub
XRY (XAMN) – Mobile Forensics and Data Recovery Software: https://www.msab.com/product/xry-extract/
Retrieving the optimal forensic data is what matters. XRY recovers data fast, in a secure, efficient, and lawful manner. XRY Logical. XRY Physical. XRY Pro. XRY Photon. XRY Cloud. XRY PinPoint. XRY Camera.

X-Ways Forensics: https://www.x-ways.net/
Integrated computer forensics environment. Our flagship product, based on WinHex.

X-Ways Forensics: https://www.x-ways.net/
Disk imaging, disk cloning, virtual RAID reconstruction. Best speed, most intelligent compression.

X-Ways Investigator: https://www.x-ways.net/investigator/index-m.html
Reduced, simplified version of X-Ways Forensics for police investigators, lawyers, auditors, ...

WEBINÁRIOS


Webinar - Academia de Forense Digital
Por Daniel Avilla | Academia de Forense Digital| Março 2022
Apresentação de ferrramentas: Avila Forensics, Bytecode Viewer, Andriller, ...

PODCASTS


Podcast - FTK Mobile, Cellphone Forensics Tool Comparisons, and New Open Source Artifacts.
Competition is Heating Up in the Mobile Forensics Space.
By Heather Charpentier & Alexis "BRIGS" Brignoni | Digital Forensics Now | October 05, 2023


Podcast - How can DigitalL Evidence help solve crime?
By Heather Charpentier & Alexis "BRIGS" Brignoni | Magnet Forensics| October 05, 2023
Join investigators, examiners, and prosecutors as they share the riveting cases that helped define their careers and how digital forensics played a pivotal part in the investigation.


PADRÕES


NIST - Recommendation: Closed Circuit Television (CCTV) Digital Video Export Profile - Level 0 (Revision 1)
This document updates and replaces NISTIR 8161. This revised recommendation continues to focus on storing metadata to support video analytics. At the FBI's request, NIST conducted research and developed NISTIR 8161 as a recommendation to address the FBI's minimum interoperability requirements for the exporting and exchange of video recordings captured by closed circuit television (CCTV) digital video recording (DVR) systems. NIST termed these requirements "Level 0". Subsequently, NIST shared its findings and recommendations with video industry hardware and software manufacturers, and the relevant standards community.

IEC - IEC 62676-2-31:2019
Video surveillance systems for use in security applications - Part 2-31: Live streaming and control based on web services
This document defines procedures for communication between network video clients and video transmitter devices.

PROGRAMAS DE PESQUISA, DESENVOLVIMENTO E INOVAÇÃO


P&D - TITANIUM PROJECT - Tools for the Investigation of Transactions in Underground Markets.
TITANIUM has closed on 2020-04-30.



Competition is Heating Up in the Mobile Forensics Space.
By Heather Charpentier & Alexis "BRIGS" Brignoni | Digital Forensics Now | October 05, 2023


By Heather Charpentier & Alexis "BRIGS" Brignoni | Magnet Forensics| October 05, 2023
Join investigators, examiners, and prosecutors as they share the riveting cases that helped define their careers and how digital forensics played a pivotal part in the investigation.



NIST - Recommendation: Closed Circuit Television (CCTV) Digital Video Export Profile - Level 0 (Revision 1)
This document updates and replaces NISTIR 8161. This revised recommendation continues to focus on storing metadata to support video analytics. At the FBI's request, NIST conducted research and developed NISTIR 8161 as a recommendation to address the FBI's minimum interoperability requirements for the exporting and exchange of video recordings captured by closed circuit television (CCTV) digital video recording (DVR) systems. NIST termed these requirements "Level 0". Subsequently, NIST shared its findings and recommendations with video industry hardware and software manufacturers, and the relevant standards community.
IEC - IEC 62676-2-31:2019
Video surveillance systems for use in security applications - Part 2-31: Live streaming and control based on web services
This document defines procedures for communication between network video clients and video transmitter devices.


TITANIUM has closed on 2020-04-30.
